Phoronix: Mathew Garrett On The State Of Boot Security
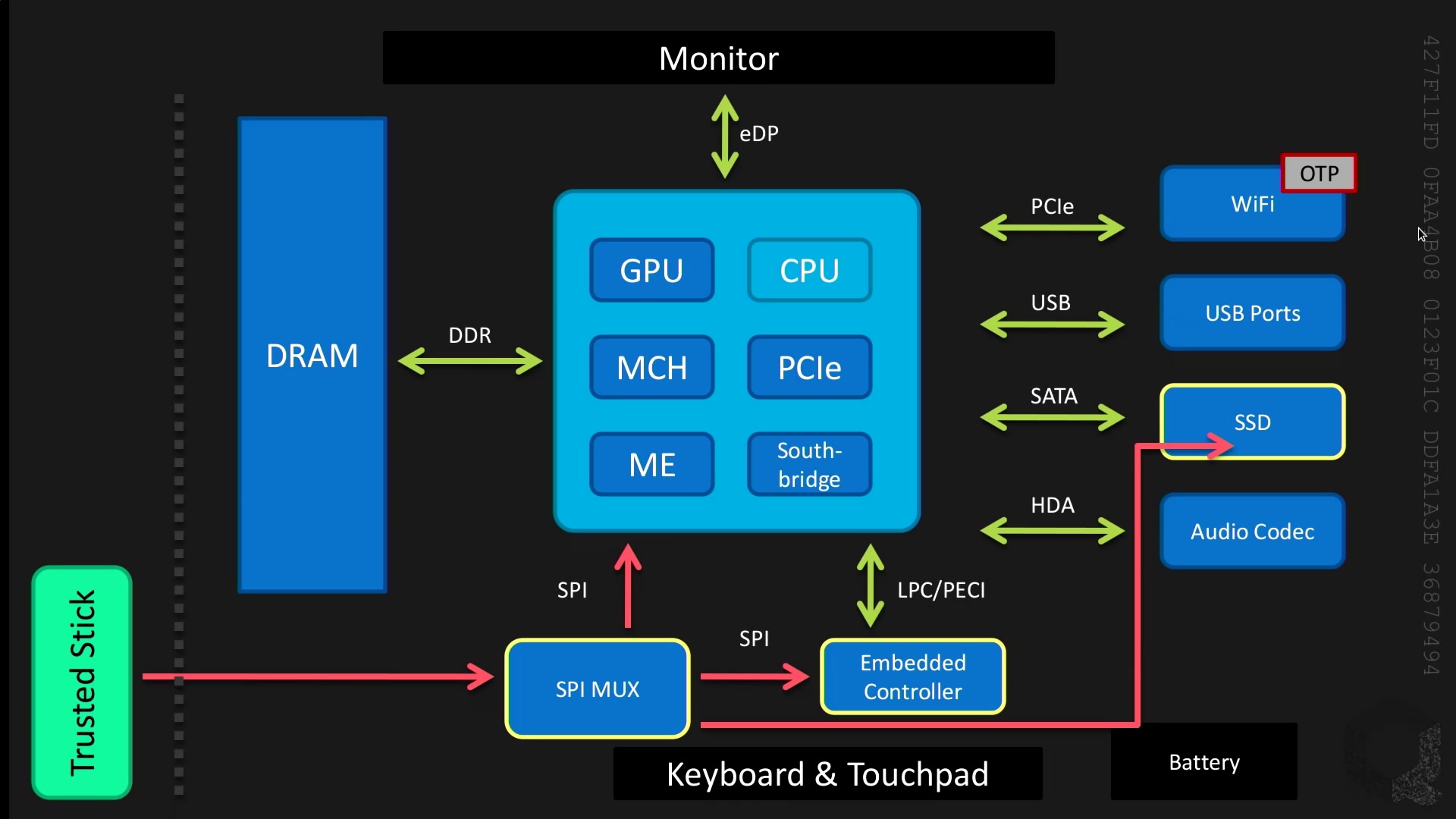
Matthew Garrett presented this week at the Chaos Computer Club's 32C3 conference about the state of boot security...
Matthew Garrett presented this week at the Chaos Computer Club's 32C3 conference about the state of boot security...

Comment